Expressing Which Two Attack Tree Characteristics Clearly Can Most Increase the Tree's Value?
Attack Copse
Dr. Dobb's Periodical, December 1999.
Modeling security threats
Past Bruce Schneier
Few people truly empathize calculator security, equally illustrated by computer-security company marketing literature that touts "hacker proof software," "triple-DES security," and the like. In truth, unbreakable security is cleaved all the time, often in means its designers never imagined. Seemingly strong cryptography gets broken, too. Attacks thought to be beyond the ability of mortal men get commonplace. And as newspapers report security bug subsequently security bug, it becomes increasingly articulate that the term "security" doesn't have meaning unless as well yous know things similar "Secure from whom?" or "Secure for how long?"
Clearly, what we need is a mode to model threats confronting computer systems. If nosotros can understand all the dissimilar ways in which a system can be attacked, nosotros can likely design countermeasures to thwart those attacks. And if nosotros can understand who the attackers are — not to mention their abilities, motivations, and goals — maybe we tin can install the proper countermeasures to deal with the existent threats.
Enter Attack Trees
Attack trees provide a formal, methodical fashion of describing the security of systems, based on varying attacks. Basically, you represent attacks against a system in a tree structure, with the goal as the root node and unlike means of achieving that goal as leaf nodes.
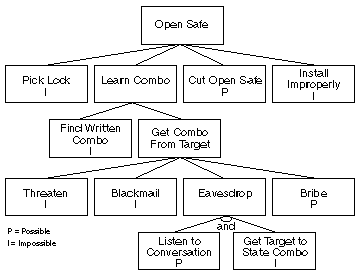
Figure 1: Assault Nodes
Figure 1, for instance, is a elementary attack tree against a physical safe. The goal is opening the safe. To open the safe, attackers can pick the lock, acquire the combination, cutting open up the safe, or install the prophylactic improperly so that they tin easily open information technology later on. To larn the combination, they either accept to find the combination written down or get the combination from the safe possessor. So on. Each node becomes a subgoal, and children of that node are ways to achieve that subgoal. (Of course, this is just a sample attack tree, and an incomplete one at that. How many other attacks can you remember of that would reach the goal?)
Notation that there are AND nodes and OR nodes (in the figures, everything that isn't an AND node is an OR node). OR nodes are alternatives — the 4 ways to open up a rubber, for example. AND nodes represent different steps toward achieving the same goal. To eavesdrop on someone saying the condom combination, attackers have to eavesdrop on the conversation AND get safe owners to say the combination. Attackers can't achieve the goal unless both subgoals are satisfied.
That'due south the bones assault tree. Once you take it completed, you can assign values — I (impossible) and P (possible) in Figure i — to the various leaf nodes, then make calculations about the nodes. (Again, this is simply an illustrative example; practice not take the values as an indication of how secure my safe really is.) Once you assign these values — presumably this assignment will exist the result of painstaking research on the safe itself — you can summate the security of the goal. The value of an OR node is possible if any of its children are possible, and incommunicable if all of its children are impossible. The value of an AND node is possible only if all children are possible, and impossible otherwise; come across Figure two.
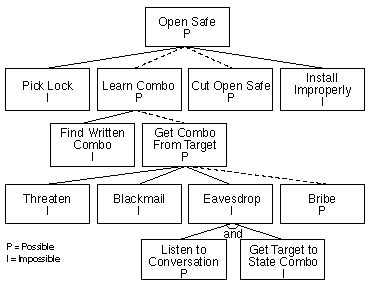
Figure 2: Possible Attacks
The dotted lines in Figure 2 show all possible attacks — a hierarchy of possible nodes, from a leaf to the goal. In this sample system, at that place are two possible attacks: Cutting open the safe, or learning the combination by bribing the owner of the safe. With this knowledge, you lot know exactly how to defend this organisation against set on.
Assigning "possible" and "impossible" to the nodes is but ane way to look at the tree. Whatsoever Boolean value tin exist assigned to the leaf nodes and then propagated up the tree construction in the same manner: easy versus difficult, expensive versus inexpensive, intrusive versus nonintrusive, legal versus illegal, special equipment required versus no special equipment. Figure 3 shows the same tree with some other Boolean node value.
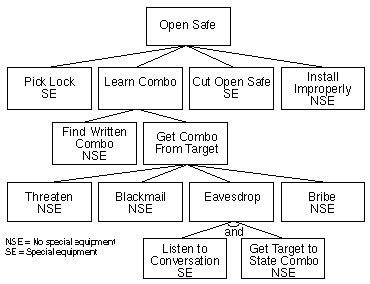
Figure 3: Special Equipment Required
Assigning "expensive" and "not expensive" to nodes is useful, but it would be better to prove exactly how expensive. Information technology is also possible to assign continuous values to nodes. Figure 4 shows the tree with different costs assigned to the leaf nodes. Like Boolean node values, these tin can propagate upwards the tree too. OR nodes have the value of their cheapest child; AND nodes have the value of the sum of their children. In Effigy 4, the costs have propagated up the tree, and the cheapest attack has been highlighted.
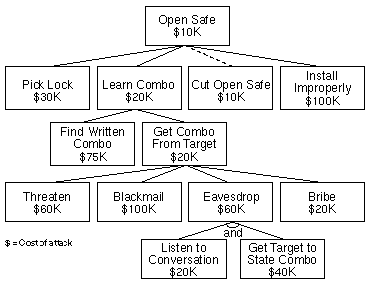
Figure 4: Cost of Assail
Again, this tree tin can be used to determine where a system is vulnerable. Effigy 5 shows all attacks that toll less than $100,000. If you are only concerned with attacks that are less expensive (mayhap the contents of the safe are just worth $100,000), then you lot should only business organization yourself with those attacks.

Figure 5: All Attacks Less than $100,000
There are many other possible continuous node values, including probability of success of a given attack, likelihood that an attacker will try a given assault, and and so on.
Nodes and Their Values
In any existent attack tree, nodes will have many different values corresponding to many dissimilar variables, both Boolean and continuous. Different node values can be combined to larn even more virtually a arrangement's vulnerabilities. Figure half dozen, for instance, determines the cheapest attack requiring no special equipment. You tin can also find the cheapest depression-chance assault, most probable nonintrusive attack, all-time low-skill attack, cheapest attack with the highest probability of success, most probable legal attack, so on. Every time you query the attack tree almost a certain feature of attack, you larn more than about the organization's security.

Figure 6: Cheapest Assault Requiring No Special Equipment
To make this work, yous must marry attack trees with knowledge about attackers. Different attackers have unlike levels of skill, admission, run a risk aversion, money, and and then on. If you're worried about organized crime, y'all accept to worry about expensive attacks and attackers who are willing to get to jail. If you are worried about terrorists, you lot besides have to worry about attackers who are willing to die to attain their goal. If you lot're worried about bored graduate students studying the security of your system, you normally don't have to worry almost illegal attacks such as bribery and blackmail. The characteristics of your attacker determine which parts of the attack tree you have to worry virtually.
Attack trees also let yous play "what if" games with potential countermeasures. In Effigy 6, for example, the goal has a cost of $20,000. This is because the cheapest set on requiring no special equipment is bribing the person who knows the combination. What if you implemented a countermeasure — paying that person more so that he is less susceptible to bribes? If yous presume that the cost to ransom him is now $80,000 (again, this is an example; in the existent world you'd exist expected to research exactly how a countermeasure affects the node value), and then the toll increases to $threescore,000 (presumably to hire the thugs to practise the threatening).
A PGP Instance

Effigy 7: Assail Tree Against PGP
Effigy 7 is an attack tree for the popular PGP eastward-mail security program. Since PGP is a circuitous program, this is a complex tree, and it's easier to write information technology in outline course than graphically. PGP has several security features, so this is only ane of several assault trees for PGP. This item assail tree has "read a message encrypted with PGP" equally its goal. Other goals might be: "forge someone else'southward signature on a bulletin," "change the signature on a message," "undetectibly alter a PGP-signed or PGP-encrypted message," and and then on.
What immediately becomes credible from the assault tree is that breaking the RSA or Idea encryption algorithms are not the most assisting attacks against PGP. There are many ways to read someone'southward PGP-encrypted letters without breaking the cryptography. You tin capture their screen when they decrypt and read the messages (using a Trojan equus caballus like Back Orifice, a Tempest receiver, or a secret camera), grab their private key later on they enter a passphrase (Back Orifice again, or a dedicated reckoner virus), recover their passphrase (a keyboard sniffer, Tempest receiver, or Back Orifice), or simply try to animal force their passphrase (I tin can assure you that it will take much less entropy than the 128-bit IDEA keys that it generates). In the scheme of things, the pick of algorithm and the key length is probably the least important thing that affects PGP's overall security. PGP not only has to be secure, just it has to be used in an environment that leverages that security without creating whatever new insecurities.
Creating Attack Copse
How do you create an attack tree like this? First, you identify the possible assail goals. Each goal forms a separate tree, although they might share subtrees and nodes. Then, try to think of all attacks confronting each goal. Add together them to the tree. Repeat this process downward the tree until you are done. Requite the tree to someone else, and have him think about the process and add whatever nodes he thinks of. Repeat every bit necessary, possibly over the grade of several months. Of course there'southward ever the chance that you forgot about an assail, but you'll get better with fourth dimension. Like any security analysis, creating attack trees requires a certain mindset and takes do.
Once yous have the attack tree, and take researched all the node values (these values will alter over fourth dimension, both as attacks become easier and as you become more exact data on the values), you can utilize the attack tree to make security decisions. You can look at the values of the root node to see if the system's goal is vulnerable to attack. You can decide if the system is vulnerable to a item kind of assail; password guessing, for example. You can use the attack tree to list the security assumptions of a system; for instance, the security of PGP might assume that no one could successfully bribe the programmers. You can determine the touch on of a system modification or a new vulnerability discovery: Recalculate the nodes based on the new information and run into how the goal node is affected. And y'all can compare and rank attacks — which is cheaper, which is more than likely to succeed, and the like.
One of the surprising things that comes out of this kind of analysis is that the areas people call back of equally vulnerable usually aren't. With PGP, for case, people generally worry most key length. Should they utilize 1024-bit RSA or 2048-fleck RSA? Looking at the attack tree, though, shows that the key length of RSA doesn't really matter. At that place are all sorts of other attacks — installing a keyboard sniffer, modifying the plan on the victim'southward hard drive — that are much easier than breaking the RSA public key. Increasing the cardinal length from 1024 bits to 2048 $.25 is like putting an enormous stake into the ground and hoping the enemy runs right into it, equally opposed to edifice a lower palisade around the target. Assault trees give y'all perspective on the whole system.
1 of the things that really makes attack trees valuable is that they capture noesis in a reusable form. Once you lot've completed the PGP assail tree, you can use it in whatsoever situation that uses PGP. The assail tree confronting PGP becomes part of a larger assail tree. For example, Figure 8 shows an set on tree whose goal is to read a specific message that has been sent from one Windows 98 calculator to another. If yous expect at the root nodes of the tree, the entire assail trees for PGP and for opening a rubber fit into this set on tree.

Figure 8: Set on Tree Against a General Computer System
This scalability ways that you don't have to be an practiced in everything. If y'all're using PGP in a system, you don't have to know the details of the PGP attack tree; all you need to know are the values of the root node. If you're a computer-security expert, y'all don't have to know the details about how difficult a detail model of condom is to crack; you just need to know the values of the root node. Once you build up a library of attack trees against particular computer programs, door and window locks, network security protocols, or whatever, you can reuse them whenever you need to. For a national security agency concerned near compartmentalizing attack expertise, this kind of organisation is very useful.
Conclusion
Attack copse provide a formal methodology for analyzing the security of systems and subsystems. They provide a way to call up well-nigh security, to capture and reuse expertise virtually security, and to respond to changes in security. Security is not a product — it's a process. Attack trees grade the basis of understanding that process.
Categories: Miscellaneous Papers
Sidebar photo of Bruce Schneier by Joe MacInnis.
Source: https://www.schneier.com/academic/archives/1999/12/attack_trees.html
0 Response to "Expressing Which Two Attack Tree Characteristics Clearly Can Most Increase the Tree's Value?"
Post a Comment